INTRODUCTION
Fresh cybersecurity threats coming from AI and automation
On December 8, 2022, the US Office of Health and Human Services (HHS) Office of Information Security’s Health Sector Cybersecurity Coordination Center (HC3) released a detailed brief titled ‘Automation and Hacking: Potential Impacts on Healthcare.’ According to the HC3, healthcare organizations face substantial automated threats involving social engineering operations, phishing, spear phishing attempts, credential stuffing, brute force attacks, and many other new forms of artificial intelligence-generated malware.
Malicious threat actors have leveraged automation to launch attacks with global reach at scale. Hackers use automation at scale to identify personal information, financial data, medical research, and corporate data
At least 590 provider organizations have reported personal health information (PHI) data breaches to the HHS’s Office for Civil Rights (OCR) since the start of 2022. The losses impacted 48.6 million individual records—up from just 40 million in 2021.
Cyber criminals leverage artificial intelligence to design better malware that is not easy to detect, isolate, and mitigate. To respond, cybersecurity specialists use machine learning-enabled penetration testing tools to proactively scan the threat environment.
In this post, learn more about HC3’s perspectives on what healthcare organizations need to do to protect their organizations from the pervasive and rapidly expanding landscape of automated hacking threats.
OPEN SOURCE
Open source: Systems are targets, tools are hacking aids
Hospitals that use open-source software are often easy targets for hackers. Known vulnerabilities, compromise of legitimate packages, and name confusion attacks are the main risks.
Malicious threat actors launch cyber-attacks against healthcare enterprises using a variety of open-source automated cyber attack tools, too. It is the misuse of software made freely available to professionals for intended use. Let us take a closer look at some examples:
Nmap: An open-source tool to map, audit, and scan networks for security, it is used both by ethical hackers and by bad actors to find and exploit vulnerabilities.
Wireshark: A real-time network protocol analyzer, it is used by hackers for malicious actions, including seeking confidential information.
Legion: An extensible and semi-automated network penetrating tool; a namesake credential harvester based on Python also exists.
Scapy: A network manipulation tool that provides both defenders and attackers network modification packages -hackers may use it to send fake information and receive responses.
Nikto2: A tool for web server scanning -but it may be misused to target those with vulnerabilities.
Other useful open-source tools like Jok3r, Zed Proxy, Attack 11,Nikto2, OpenSCAP,Sqlmap, and CrackStation can be manipulated for use with malicious intent
Today’s cybersecurity threat landscape is unlike ever seen before. Private health information is one of the most lucrative targets for criminals interested in making quick money, offering crime ware-as-a-service (CaaS).
VULNERABILITIES
Supply chain attacks are on the rise
Since the start of 2022, 99% of cyber-attacks targeting healthcare organizations were launched through their supply chains. Supply chain cyber-attacks launched against third-party vendors can have devastating consequences as attacks complete lateral movements to gain further access to system resources.
The vast majority of cyber-attacks launched against healthcare organizations today are perpetrated using automated software solutions. Automation offers incredible benefits for healthcare organizations but also provides adversarial hackers with the firepower they need to launch attacks around the clock, at scale, using highly advanced, metamorphic structures that are extremely difficult to defend against.
Supply chain attacks against healthcare providers succeed by penetrating an organization’s weakest links. This form of cybercrime is a type of island-hopping attack that hackers launch in hopes of gaining greater access to vital system resources and data, which can be used to infect other businesses in the supply chain.
MITIGATION
Managing cybersecurity risk in the digital health ecosystem
Safeguarding your healthcare organization with custom software solutions against the threat of cyber-attacks is essential to fulfilling corporate risk management criteria. Countering the persistent threat of cyber-attacks requires that a healthcare organization should adopt a holistic approach and leverage the positive defensive benefits of automation. Implementing cyber security best practices at every level of a healthcare organizational structure is the most critical measure to be taken.
Medical devices, digital health apps, and electronic health record (EHR) software are just a few entry points for criminal hackers. It is essential for healthcare organizations to adopt modern cybersecurity strategies such as two-factor authentication, zero-trust frameworks, end-point security, and the cyber kill chain defensive posture developed by Lockheed Martin (See infographic below)
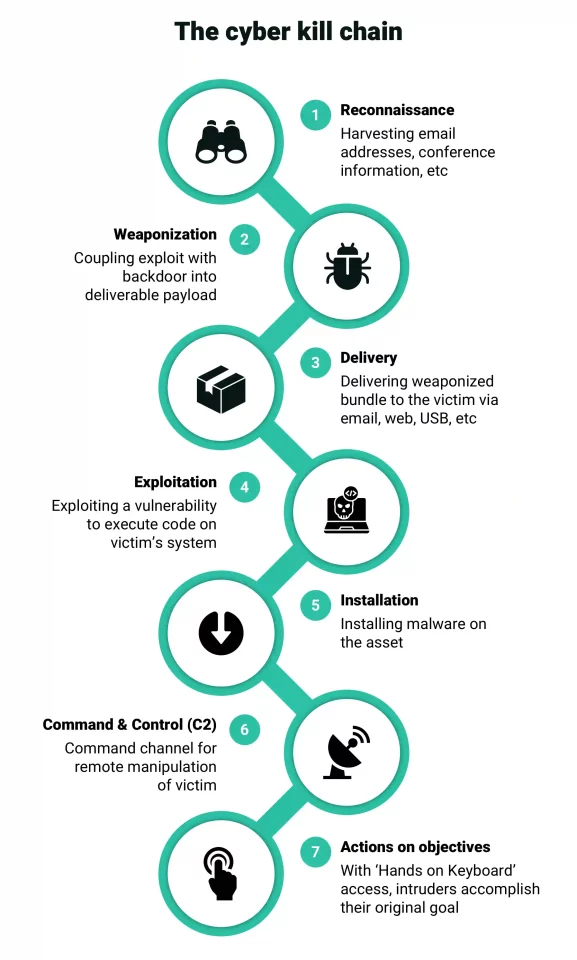
Understand the actions an adversary has to perform to complete an attack Source
Managing cybersecurity risk across the digital health ecosystem requires:
- Constantly evaluating, analyzing, and responding to risks posed by third parties. These efforts should be intelligent, coordinated, and ongoing.
- Constantly evaluating the system resources that employees, third-party contractors, or suppliers require access to. Reduce the number of individuals responsible for installing and modifying third-party software solutions.
- Emphasize supply chain-wide response and remediation plans to ensure a fast response time and manage the damage of an attack.
- Review who has access to what organizational data. Information security is mission-critical to the success of your healthcare organization.
- Ensure your third-party vendors are practicing proper data security best practices when handling your organization’s information.
- Invest in professionals, tools, and training opportunities to improve your organization’s cyber resilience. Improving cybersecurity is an ongoing quality assurance process.
THIRD PARTIES
Develop custom healthcare solutions to remove third-party risk
Your healthcare organization is only as secure as your partners. Third-party risks place all healthcare providers at unnecessary risk. Hackers threaten the success of healthcare and limit an organization’s potential for growth by discovering and exploiting the vulnerabilities of their vendors. Safeguarding your healthcare enterprise against third-party risk is an essential part of risk management.
It is not just about protecting patient health information -data breaches are just one cyber-security risk for a healthcare organization. The reliance on cloud tools and services and remote monitoring systems poses a risk to operations as well. Here are five things you should do at the vendor’s end to ensure there is no risk to your own business operations.
- Carry out a detailed vendor risk assessment for HIPAA compliance.
- Spell out data security procedures in the contract.
- Cross-check periodically for robust authentication and encryption protocols.
- Insist on regular reports with continuous monitoring.
- Check if the employee training program is up and running for new staff.
CONCLUSION
Healthcare cybersecurity: Better safe than sorry
In addition to the above, it is important to have some things done at your end, too. First, network segmentation with access controls for each stream of traffic;secondly, make sure to put in place a business continuity and healthcare technology security plan; thirdly, craft a lifecycle management strategy that ensures third parties do not retain data or access rights after the end of a relationship; and lastly, make it a practice to the monitor the news for cyber incidents at the supplier end. Remember, when it comes to cybersecurity in healthcare, it is better to be safe than sorry.






